Your Data. Your AI. Your Rules.
Transform your data into real-time intelligence without vendor lock-in. Our open Lakehouse platform powers fraud detection, revenue assurance, and AI driven insights for enterprises that demand security, speed, and complete data sovereignty.
Enterprise Clients
Projects Delivered
Years Experience
Uptime SLA
100% Open Lakehouse
Apache Spark, Iceberg, Trino - own your stack. No proprietary formats. No exit fees. Full portability.
Weeks, Not Months
Pre-built connectors for telecom, finance & enterprise. Go from raw data to production dashboards in 4-6 weeks.
Bank-Grade Security
SOC2 compliant. End-to-end encryption. Fine-grained access control. Your data never leaves your infrastructure.
From Raw Data to Real-Time Insights
Our comprehensive data pipeline transforms raw data from multiple sources into actionable intelligence through advanced processing, storage, and AI-powered analytics.
Data Collection
Multiple data sources
Clean & Validate
Data quality & validation
Data Lakehouse
Unified storage layer
Transform
ETL & processing
AI/ML
Intelligence & insights
Real-time Analytics
Insights & monitoring
Proven Solutions Across Critical Industries
Lakehouse-powered analytics for telecommunications, financial services, regulators, and enterprises
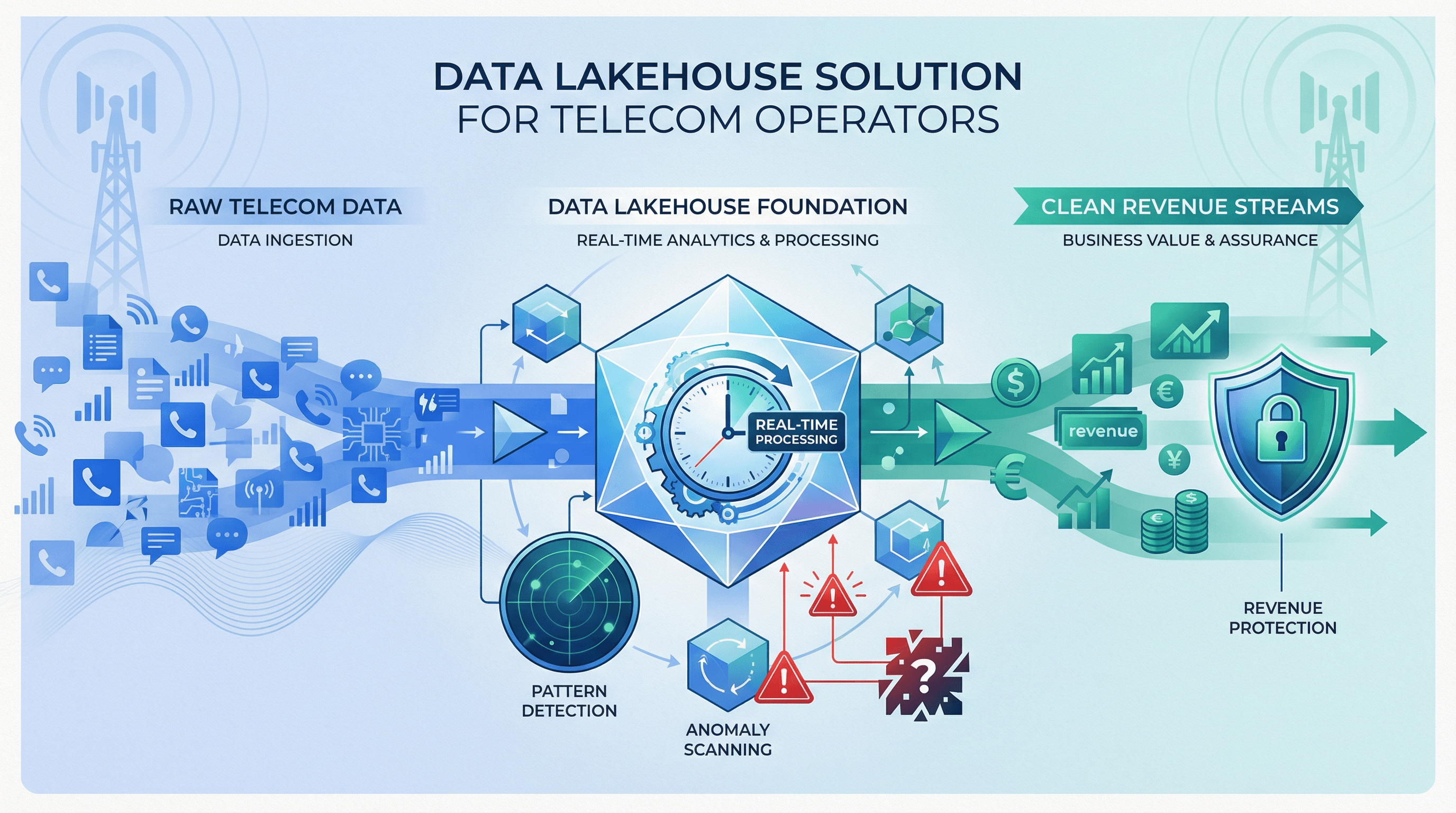
Telecom Operators
From revenue assurance to network optimization, process 12B+ CDRs daily on one platform. Reduce revenue leakage by 15%, detect fraud in under 1 minute, monitor QoS in real-time, and secure mobile money transactions. All with enterprise-grade security and proven telecom expertise.
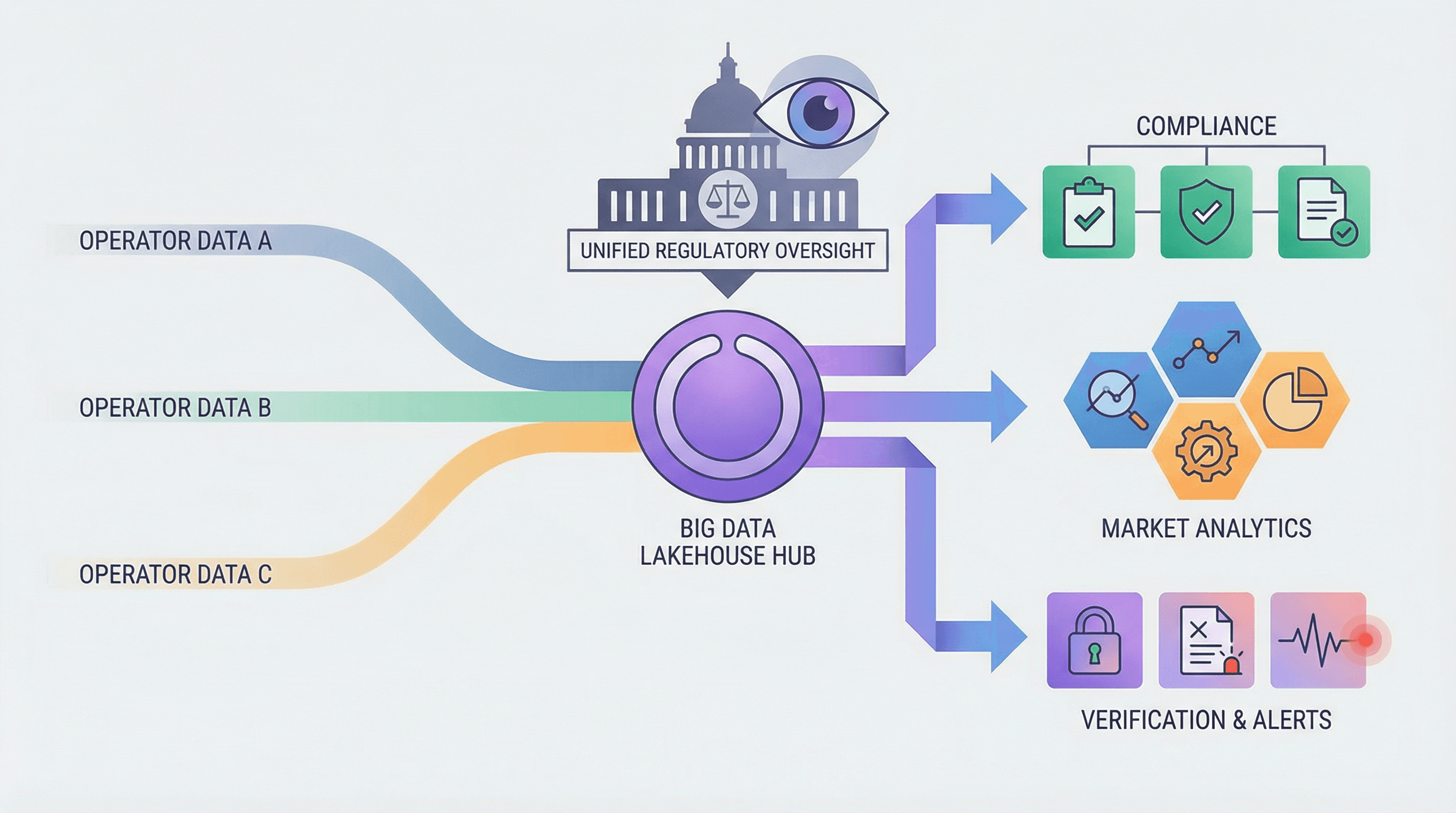
Regulators & Governments
Monitor all operators on one unified platform. Aggregate and analyze data from multiple licensees to detect market manipulation, verify tax compliance with accuracy, identify cross-operator fraud patterns in real-time, and enforce QoS standards with automated reporting and audit trails.
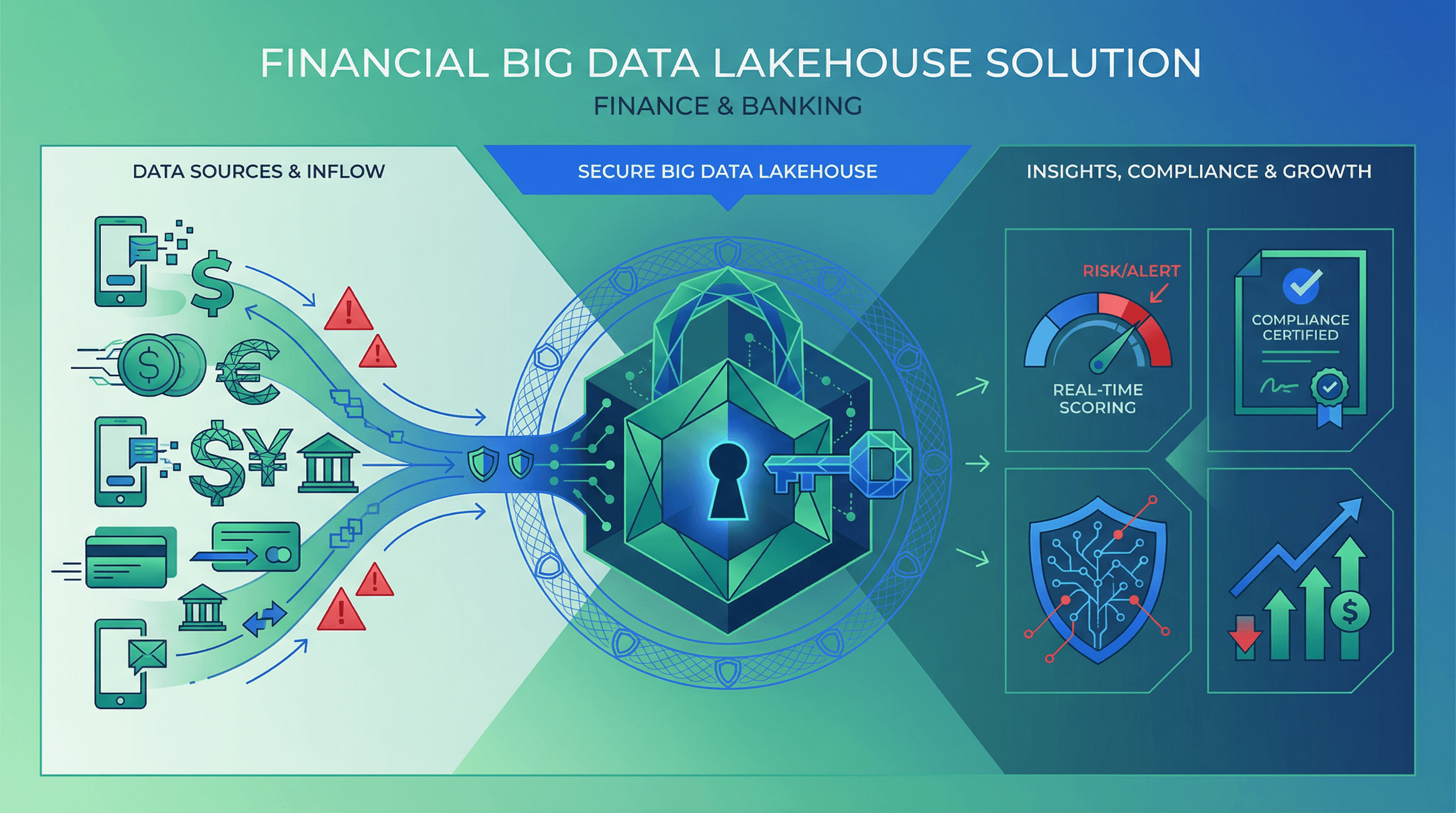
Financial Services
Fraud detection accuracy across millions of daily transactions. Our platform delivers real-time monitoring of P2P transfers, agent networks, merchant payments, and cash operations - with automated suspicious activity detection, transaction pattern analysis, and risk scoring. Keep mobile money safe, compliant, and trusted.
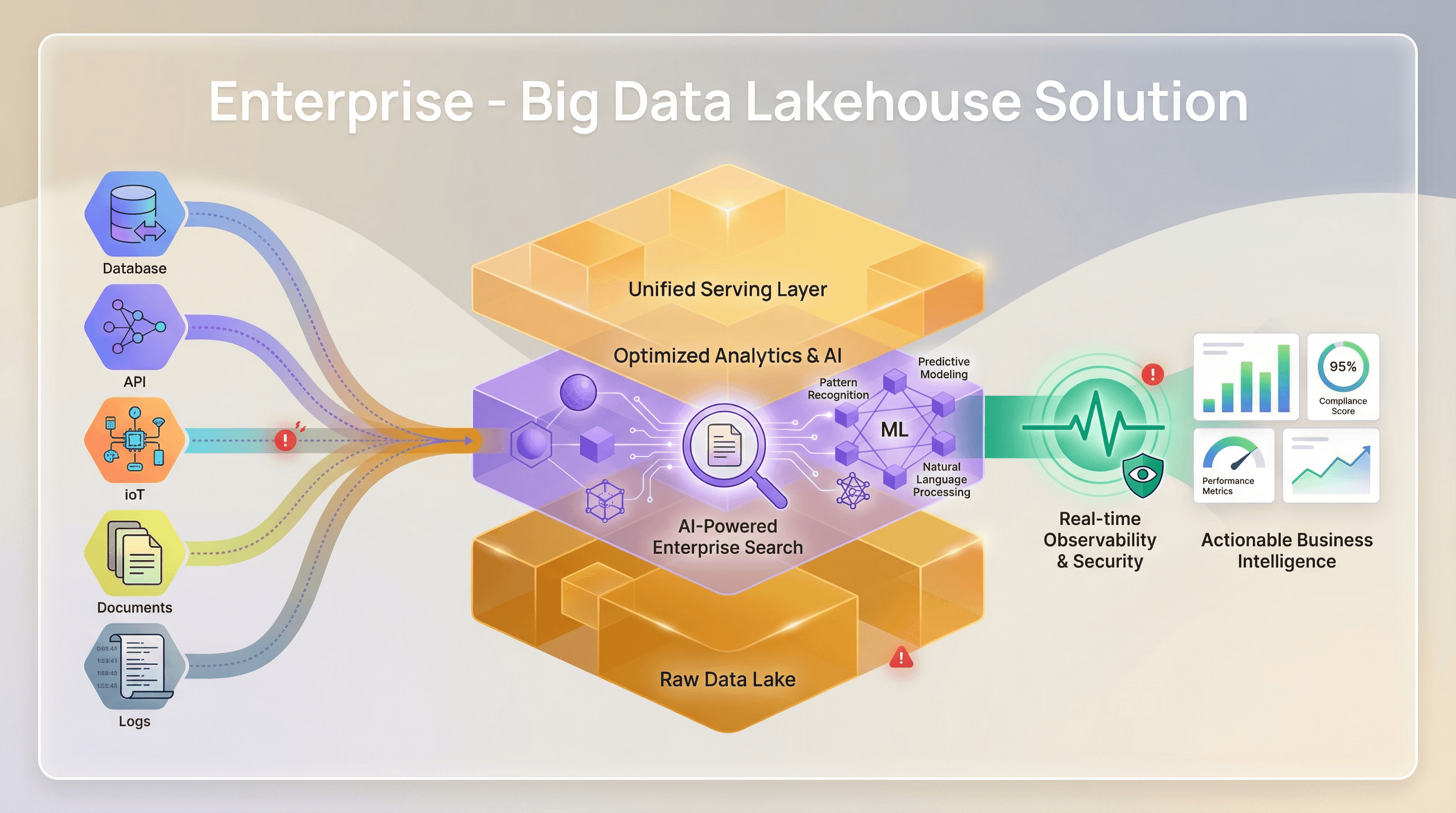
Enterprises
From AI-powered search to security operations—unify all your data on a single platform. Leverage RAG/LLM for intelligent insights, monitor system health with comprehensive observability, detect threats with 99.7% accuracy through SIEM analytics, and power business intelligence across the enterprise. All on secure, governed lakehouse architecture.
Our Technology Stack
Powered by Leading Open-Source Technologies
We leverage cutting-edge open-source technologies that ensure no vendor lock-in, maximum flexibility, and long-term cost efficiency. Select the best-fit tools for each step of your data journey.
Data Processing & Ingestion
Real-time data ingestion, transformation, and streaming
Apache NiFi
Data flow automation
Apache Spark
Large-scale data processing
Apache Flink
Stream processing
Apache Kafka
Event streaming platform
Redpanda
Kafka-compatible streaming
On-Premise Storage & Compute
Enterprise-grade on-premise infrastructure, storage, and compute
Apache Ozone
Distributed object store
MinIO
High-performance object storage
Dell (PowerScale, PowerEdge)
Enterprise storage and servers
Docker
Containerization platform
Kubernetes
Container orchestration
Distributed SQL Engine
High-performance distributed query engines
Starburst
Enterprise Trino distribution
Trino
Distributed SQL query engine
Presto
Distributed SQL query engine
Lakehouse Open Table Format
Modern table formats for data lakehouses
Apache Hudi
Incremental data processing
Apache Iceberg
Table format for analytics
Delta Lake
ACID transactions for data lakes
Data Consumption & Visualization
Business intelligence and data visualization
Power BI
Microsoft BI platform
Apache Superset
Open-source BI platform
Grafana
Observability dashboards
Orchestration & ETL
Workflow orchestration, data transformation, and pipeline management
Apache Airflow
Workflow orchestration platform
Dagster
Data orchestration platform
dbt
Data transformation tool
Data Science & ML
Machine learning and experimentation platforms
Jupyter
Interactive notebooks
MLflow
ML lifecycle management
Amazon SageMaker
Fully managed ML service
Observability & Search
Logging, monitoring, and search capabilities
Elasticsearch
Search and analytics engine
OpenSearch
Open-source search engine
Prometheus
Open-source systems monitoring and alerting
Technology Agnostic Approach
We select the best technology stack for your specific needs, whether it's ELK Stack for search and analytics, Apache ecosystem for data processing, or a hybrid approach combining multiple technologies.
Enterprise-Grade Architecture
Comprehensive data platform solutions designed for regulatory compliance, operational excellence, and scalable performance across mission-critical environments.
AI & ML Algorithms
Advanced neural networks process data streams to detect fraud, analyze revenue patterns, and ensure compliance. Our AI algorithms provide real-time insights with interconnected processing nodes.
Cloud-Native Infrastructure
Auto-scaling Kubernetes infrastructure with containerized applications that expand and contract based on data load. Multiple cloud layers ensure high availability and resilient operations.
Modern Data Lakehouse
Unified data architecture where structured, semi-structured, and unstructured data flows through processing layers into a centralized lakehouse storage system with ACID compliance.
Enterprise Search
Intelligent search engine that scans across all data assets with lightning speed. Visual scanning shows real-time results discovery across logs, metrics, documents, and structured data.
Real-Time Analytics
Live monitoring dashboards with neural network processing to detect anomalies, track performance metrics, and provide operational intelligence across your data ecosystem.
Log Analytics
Comprehensive log analysis using AI-powered pattern recognition to transform system logs into actionable intelligence for security monitoring and performance optimization.
End-to-End Data Pipeline Architecture
Ingestion
Real-time & Batch
Processing
Transform & Enrich
Storage
Lakehouse Architecture
Analytics
Insights & Visualization
ACID Compliant
Ensure data consistency and reliability
Enterprise Security
Bank-level encryption and access control
Real-time Processing
Sub-second latency for critical operations
Why Choose Synaptique?
Experience the power of open-source data solutions with enterprise-grade reliability, regulatory compliance, and unmatched flexibility for your critical operations.
Open-Source Excellence
Build on proven open-source technologies with no vendor lock-in. Maintain full control and flexibility over your data infrastructure.
Rapid Deployment
Get up and running quickly with our agile methodology. From pilot to production in weeks, not months.
Enterprise-Grade Security
Bank-level security and compliance built into every solution. Meet regulatory requirements across telecommunications, finance, and government sectors.
Proven Expertise
15+ years of experience delivering mission-critical data solutions. Deep domain expertise in telecom, finance, and regulatory compliance.
Scalable Architecture
Built to scale from thousands to billions of events. Cloud-native and on-premise deployment options to fit your needs.
End-to-End Support
24/7 monitoring, dedicated support, and continuous optimization. We're your partner for the long term, not just implementation.
Trusted by Industry Leaders
From telecom operators managing billions of CDRs to financial institutions processing millions of transactions daily, our solutions power mission-critical operations across industries.
Proven Success Stories
Real-world implementations delivering measurable business impact
Protecting Networks in Central Africa from SIMbox Bypass Fraud
Telecommunications • Fraud Detection
Successfully secured networks with real-time monitoring, restored accurate call routing, and eliminated SIMbox fraud activities
Tackling CLI Spoofing Fraud in Central Africa
Telecommunications • Fraud Detection
Secured networks against CLI spoofing attacks, restored accurate caller identification, and protected customers from deceptive practices
Preventing Revenue Loss from Untaxed Devices
Telecommunications • Fraud Detection
Delivered real-time device identity visibility and inter-agency data sharing, resulting in the recovery of over $15 million in lost tax revenue.
Trusted by Industry Leaders
Strategic partnerships with leading technology providers ensure best-in-class solutions